by John Valdés
Welcome to pilOTP, a one-time password (OTP) generator for the
U.S. Robotics Pilot.
With pilOTP and your Pilot, you'll never again be
caught logging into your computer remotely without having a OTP on
hand. Say goodbye to pre-printed lists of one-time passwords.
What are one-time passwords?
One-time passwords provide a secure way to log into networked systems
over insecure networks. A problem with traditional password
authentication systems where the same password is always used to
access the system is that when one logs into the system over a
network, the password can be observed by an eavesdropper on that
network and subsequently reused to gain unauthorized access to the
system. One-time passwords eliminate this problem by requiring a
different password for authentication each time one logs into a
system. Once a password has been used, it is no longer valid; hence,
although a network eavesdropper can capture a one-time password when
it is used to access a system over a network, it cannot be
subsequently reused since it will no longer be valid.
The passwords used by a one-time password system are computed by
combining a secret passphrase known only to the person wishing access
to the system with a "challenge" string issued by the system and then
passing this result repeatedly through a "hash" function. The output
of this function is converted into 6 short English words, and these
six words are then used as the OTP. Since the OTPs must be computed,
this means that one needs some type of password generator on a local
computer in order to calculate the appropriate OTP for accessing the
remote system. In the absence of a local computer, the alternative in
the past has been to carry a precomputed list of OTPs on a piece of
paper. Now that small, portable computers like the Pilot are
available, one can always have a computing device on hand, and with
the help of pilOTP, one can now always have an OTP generator available
ready to compute a password.
For complete information about one-time password systems, see
RFC 1938
and the references therein.
Features
- RFC 1938 compliant
- MD4, MD5 and SHA-1 support
- compatible with the S/KEY(tm) and OPIE OTP systems
- supports passphrases up to 63 characters in length
- optionally saves the last challenge used; helps save on Graffiti
strokes when repeatively computing OTPs for the same system
- optionally issues warnings when the OTP sequence number is low
(to remind you to reinitialize your OTP system) and when the
passphrase is less than 10 characters long
- given the nature of Graffiti input recognition, optionally delays
hiding of the passphrase until after it has been input
Installation
To install pilOTP in your Pilot, simply run the InstallApp program,
enter the name of the pilOTP file where indicated (or click the
Browse... button and use the dialog box to find the pilOTP.prc file)
and then click the Install button. Finally, HotSync your Pilot with
your computer to load pilOTP into your Pilot.
How to use
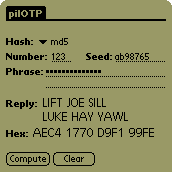 Use of pilOTP is straight-forward. First, chose the appropriate hash
function from the popup menu, then using either Graffiti strokes or
the Graffiti keyboard, enter the sequence number and seed from the
remote system challenge, enter your secret passphrase, and finally,
tap the Compute button to generate the OTP (depending on the hash and
sequence number, this may take a few seconds--the Pilot only has a
16MHz MC68K, afterall...). All the fields can be cleared at once by
tapping the Clear button. A standard Edit menu is available for
copy/paste/clear editing of individual fields (except for the
passphrase field, for which only paste and clear work). A Preferences
dialog is available for controlling the various features of the
program. Command shortcuts are available for menu commands.
Use of pilOTP is straight-forward. First, chose the appropriate hash
function from the popup menu, then using either Graffiti strokes or
the Graffiti keyboard, enter the sequence number and seed from the
remote system challenge, enter your secret passphrase, and finally,
tap the Compute button to generate the OTP (depending on the hash and
sequence number, this may take a few seconds--the Pilot only has a
16MHz MC68K, afterall...). All the fields can be cleared at once by
tapping the Clear button. A standard Edit menu is available for
copy/paste/clear editing of individual fields (except for the
passphrase field, for which only paste and clear work). A Preferences
dialog is available for controlling the various features of the
program. Command shortcuts are available for menu commands.
History
Version 1.0:
Known problems
Version 1.0:
- editing of the passphrase with the Graffiti keyboard after the
passphrase has been hidden doesn't work properly. Clear the field
first (Select All and Clear (or backspace)) before using the
keyboard.
- changing the Hide Passphrase preference after a passphrase has been
entered may cause pilOTP to lose track of the passphrase. You
will need to clear the form and re-enter the passphrase.
- stricter parsing of the number and seed fields is required;
specifically, only numerals should be allowed in the number field
(non-numerical characters can be entered with the Graffiti
keyboard), and leading and trailing spaces should be ignored from
both fields.
Planned additions
- Rework passphrase input; the field on the main form will be
replaced with a selector trigger similar to the one used for
password input in the security application. This will fix the
problems mentioned above and simplify the program a bit.
- Compress the standard dictionary. As it is now, the uncompressed
word list consumes 8K of memory, a precious commodity on the Pilot.
- Add support for a custom application code. With this, it will be
possible for pilOTP to be "called" by another Pilot application
(eg, a terminal emulator or email program) and return a computed OTP.
- Allow the computed OTP to be copied to the clipboard.
- Perhaps make the dictionary modular, so that it can be deleted (to
save memory) or replaced with a custom dictionary.
- If possible, make the hash functions modular, so that unused ones
can be deleted (to save space) and new ones added without having to
rebuild pilOTP.
- Perhaps allow the passphrase to be saved; doing so would require
that it be encrypted.
- Perhaps add decrement/increment arrows to the number field for
easy decrementing of the sequence number
- Add some type of control for scrolling the text in the seed and
passphrase fields. The fields can only be scrolled now by dragging
the stylus up or down in the field.
Legal stuff
pilOTP is Copyright © 1996 by John Valdés.
pilOTP is freeware. Permission is given for free use and distribution
of this program. Commercial distribution requires permission from the
author. No warranty is made on this software, nor is the author
liable for any damage resulting from the use of this software.
Any questions, comments or suggestions can be emailed to me at
john @ NOSPAM valdes.us.
The current version of pilOTP can be found at
http://www.valdes.us/palm/. Source code is
available on request.
Credits
Portions of pilOTP are based on the S/KEY(tm) reference implementation
written by Phil Karn, Neil M. Haller and John S. Walden, and modified
by Wietse Venema. S/KEY is a trademark of Bellcore. The MD4 and MD5
code was written by Ron Rivest. MD4 and MD5 Message-Digest Algorithms
are by RSA Data Security, Inc. The SHA-1 code is based on the
implementation written by Jim Gillogly. SHA-1 is the Secure Hash
Algorithm by the National Institute of Standards and Technology
(NIST).
Last modified: Sun Oct 6 20:24:09 1996
 Use of pilOTP is straight-forward. First, chose the appropriate hash
function from the popup menu, then using either Graffiti strokes or
the Graffiti keyboard, enter the sequence number and seed from the
remote system challenge, enter your secret passphrase, and finally,
tap the Compute button to generate the OTP (depending on the hash and
sequence number, this may take a few seconds--the Pilot only has a
16MHz MC68K, afterall...). All the fields can be cleared at once by
tapping the Clear button. A standard Edit menu is available for
copy/paste/clear editing of individual fields (except for the
passphrase field, for which only paste and clear work). A Preferences
dialog is available for controlling the various features of the
program. Command shortcuts are available for menu commands.
Use of pilOTP is straight-forward. First, chose the appropriate hash
function from the popup menu, then using either Graffiti strokes or
the Graffiti keyboard, enter the sequence number and seed from the
remote system challenge, enter your secret passphrase, and finally,
tap the Compute button to generate the OTP (depending on the hash and
sequence number, this may take a few seconds--the Pilot only has a
16MHz MC68K, afterall...). All the fields can be cleared at once by
tapping the Clear button. A standard Edit menu is available for
copy/paste/clear editing of individual fields (except for the
passphrase field, for which only paste and clear work). A Preferences
dialog is available for controlling the various features of the
program. Command shortcuts are available for menu commands.